The Intel Net
The sprawling, secretive process between sensor and action.
/https://tf-cmsv2-smithsonianmag-media.s3.amazonaws.com/filer/bc/25/bc251cf5-ff0f-491e-a575-185e97ac76e9/14n_on2016_dcgsa_live.jpg)
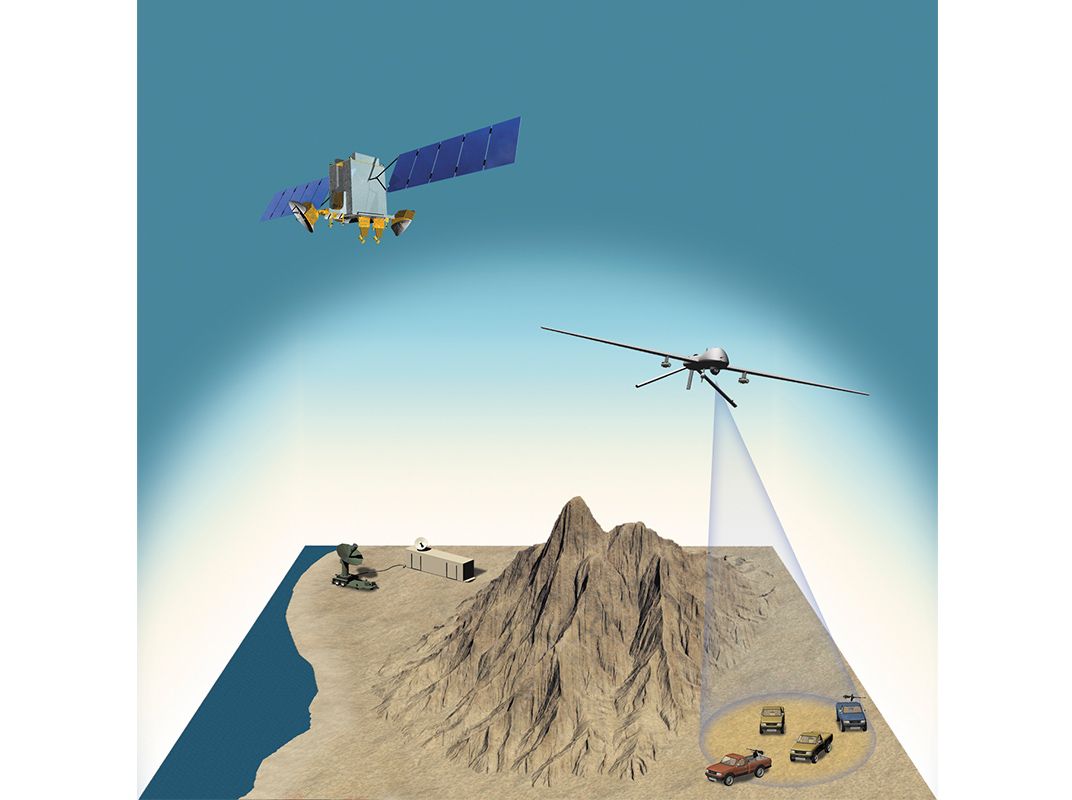
Somewhere over Afghanistan, an MQ-1B Predator, flown by a U.S. Air Force pilot half a planet away, focuses its imaging sensors on a suspicious truck driving in the mountains. Mounted below the nose of the Predator is a globe that contains an infrared sensor, electro-optical cameras, and lasers to illuminate targets for surveillance or designate them for strike aircraft. The video of the truck and the data collected by the sensors are being fed to the U.S. Air Force Distributed Common Ground System. Within seconds, the raw bits of data are transmitted by satellite and fiber-optic cable to a network of 27 centers around the world for processing, analysis, and dissemination to military units and a number of government agencies. Nearly 6,000 active and reserve air personnel, assisted by hundreds of civilian contractors, work with the data in the system.
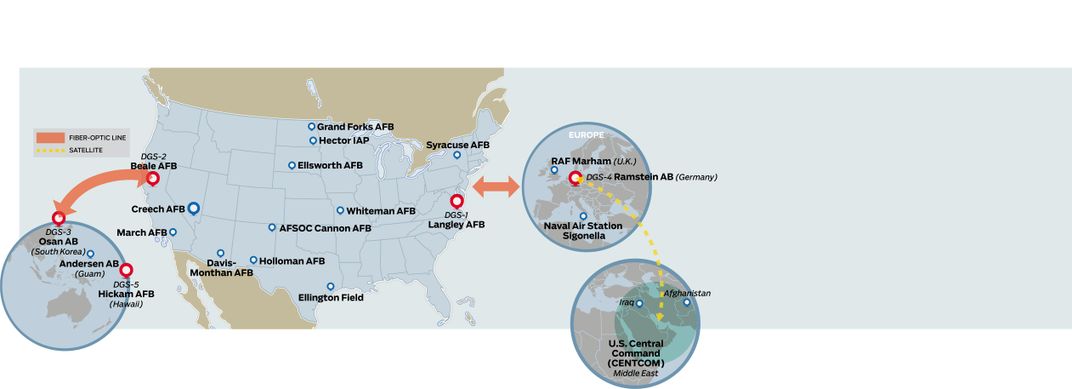
One of the units receiving the data is the 480th Intelligence, Surveillance and Reconnaissance (ISR) Wing at Joint Base Langley-Eustis in Virginia, which coordinates the network worldwide. Each facility is typically aligned with a theater of operation or type of aircraft. The distributed ground center at Langley-Eustis, designated DGS-1, focuses on imagery intelligence and electronic signals intelligence and primarily supports U.S. Central Command, or CENTCOM, which spans 20 nations, including Afghanistan. But the flow of data can instantly be redirected from one station to another. “If there’s a tornado near the Kansas center, or a backhoe hits a cable at another, we can dynamically re-task the processing,” says Don Hudson, a civilian who serves as the 480th’s technical director.
Every 24 hours, more than 20,000 gigabytes of data reach the Langley center and are handled in buildings wired with 80 miles of fiber-optic cable. The data first comes into the 480th operations center, which Hudson calls “a traffic cop.” Here some 50 staff members “make sure the ones and zeroes are flowing to the right exploitation site” in a nearby facility, says Hudson. The operations center is a high-security room where signage warns of sensitive compartmented information—“above top secret,” as some call it. During a rare open house last July, I got the chance to tour the center and observe its layout, but not the information it handles.
As I walked toward the operations center, an airman walked ahead of me waving a bright wand and shouting “Red Badge! Red Badge!” warning that someone without security clearance (and so wearing a red visitor’s badge) was approaching. Red lights swirled in the ceiling to notify those beyond earshot. Computer screens were dimmed or covered, and the four immense display screens at the front of the room, ordinarily showing video from an ISR mission, showed archived, declassified footage. Personnel had stuck pieces of duct tape over the name patches sewn on their uniforms.

Across the base in a huge, windowless warehouse, the DGS-1 processing facility can hold about 1,500 people. Inside a cavernous room at its center, about 70 analysts worked in teams of six, all enlisted personnel who appeared to be between 18 and 25 years old, supervised by one commander. The six sat in a semi-circle, called a pod, some wearing headsets. Almost all had two computer monitors at their desks. Large screens on the walls, for my visit, were set to CNN. As they watch the screens, the analysts discuss in a classified online chatroom what they see. They then type annotations summarizing the discussion onto the images.
Explains Hudson: “The analysts in the pods are speaking to a sensor control operator for the aircraft”—working at a facility such as Creech Air Force Base in Nevada for the Predator—“and talking to the air operations center in charge of the mission, and chatting with other people on that DGS floor to keep up with what else is going on in that mission.” They’re also “talking to the end users of whatever information is being collected, and to the ground component in that theater,” he says.
The first report an end user such as the NSA will see is an annotated version of images or segments of video displayed during the online chat. “When the [intelligence product] is sent to the end user, it’s also made ‘discoverable’—searchable—on the UNICORN system” he says, referring to the unified collections reporting network. A month’s worth of data and reports are kept on local servers at Langley but also copied to a master database and several backups, scattered in secret places around the continental United States. About 402,000 hours of video and 2.5 million still images are archived each year.
With so much information coming in, analysts work long hours, but shifts have recently been shortened from 14 hours to 10. The combination of monotony and short intense bursts of concentration led to burnout. The Air Force brought in a therapy dog for a few months to help relieve stress, but the newer reduced shift has also eased the tension.
Shifts are staggered at all DGS sites to assure a full staff on duty to match the busiest period in their particular theater. The pods at Langley are arranged in clusters specializing in a type of aircraft, with the largest cluster of pods focusing on the high-altitude data feeds from the U-2 and Global Hawk, both of which generate immense volumes of sensor data.
Analysts can switch airplanes and tasks but often spend several days on a single mission and eventually develop specializations in geographic locations and types of intelligence—images versus signals, say—as well as working relationships with end customers (those who requested the mission and others).
I ask Don Hudson to look back on the history of ISR collection and the period of rapid growth beginning right after 9/11. “Since the early days we had a lot of single-point failures,” when a tiny bad node in the global network could block the flow. “The biggest change is the growth in the redundancy of the architecture [of communications links] and our ability to integrate the National Guard and the reserve forces to meet joint and coalition operations,” he says. Data centers at undisclosed locations serve as backup traffic cops in the Air Force network, providing the redundancy Hudson describes.
Since the terrorist attacks of 2001, the number of Air Force ISR missions has grown from a half-dozen to more than 50 daily, or at least 20,000 missions a year. For each mission, the distributed ground system develops a tasking order to process, exploit (or analyze), and disseminate the resulting intelligence. The P-E-D tasking order assigns crews based on the aircraft chosen for the mission and the mission’s target or location. Finally, the annotated data reaches end customers, who use the intelligence products to form a picture of operations in a geographic area and to understand the intent and capability of a potential enemy.